Mobile Device Security 2011-2016: Opportunities and Challenges
10 Oct 2011 • by Natalie Aster

2011 is witnessing an explosion of new threats targeting mobile devices. Data and ID theft, SMS fraud, rogue apps and covert espionage are infecting smartphones at an unprecedented rate. Malware such as Trojans, worms, spyware and spam are spreading across mobile platforms, already highly capable of stealing data, corrupting functions and usurping control.
The research “Mobile Device Security 2011-2016: Opportunities and Challenges” by Visiongain shows that the number of mobile malware more than doubled in 2011 from 2010 with over 200 new variants in the first half of 2011 alone, out of a total of 800 since 2003.
Report Details:
Mobile Device Security 2011-2016: Opportunities and Challenges
Published: August 2011
Pages: 181
Price: US$ 2,461.00
Report Sample Abstract
Symbian
Symbian malware still represents the majority of total mobile malware. However, this is due to the early and long-standing dominance of Nokia in the handset market. It has recently shown signs of slowing growth, although new variants and families are still appearing, but at much slower rate. In essence, this is because virus creators are shifting their focus to other platforms.
Symbian Malware Growth 2009-2010
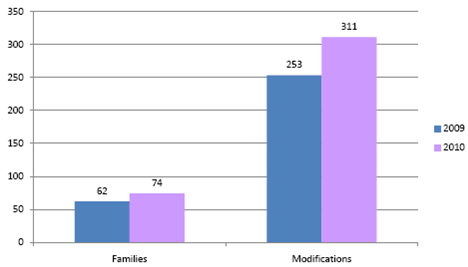
Source: Kaspersky Labs
Undeniably, the long standing presence of the Symbian platform has meant that there is a greater base of experience by malware developers. Symbian was subject to a variety of viruses, the best known of which is Cabir, the first mobile OS malware.
Symbian OS 9.x adopted a UNIX-style capability model (permissions per process, not per object). Installed software cannot perform processes unless they have been digitally signed via the Symbian Signed program. Alternatively, developers have the option of self-signing their programs.
However Symbian OS 9.x devices can be hacked to remove the platform security introduced in OS 9.1 onwards, which effectively allows users to execute unsigned code. This enables the alteration of system files, and access to previously locked areas of the OS.
iOS
There are few and little known malware targeting Apple’s iOS. However, there is a spate of different apps containing spyware. During the Network and ID Security Conference of 2011, a joint study by the Technical University of Vienna and the University of California analysed 1,400 legitimate iPhone and iPad applications in an effort to determine how much personal data was leaked by the devices. The study revealed that more than half of the apps disclosed sensitive data to third parties. Many of the apps contained standard code allowing the compilation of the user’s advertising profile.
The majority of iPhone threats however are found in jailbroken devices. Jailbreaking allows users to gain root access to the iOS. This allows users to download additional applications, extensions and themes that are unavailable through the official Apple App Store, via installers such as Cydia. In July 2011, Apple released a new version of iOS that closed the exploit used in version 3.0 of JailbreakMe, which allowed information theft through a downloaded malware by clicking on certain PDF files.
In early November 2009, the first worm for iPhone, Ike, was detected and infected both iPhones and iPod Touch devices which were jailbroken and where the default SSH password had not been changed. Ike was relatively harmless, changing the wallpaper, but a variant emerged soon afterwards. This variant copied user data and allowed remote control by the perpetrator. Users of ING Direct online banking services were targeted by a phishing site available on the device’s browser.
BlackBerry OS
In 2010, several instances of commercial spyware were released for RIM BlackBerry devices. FlexiSpy, Mobile Spy, MobiStealth, and SpyBubble all expanded to include threats targeted specifically at BlackBerry devices. These spyware applications pose a great risk to confidentiality, integrity, and availability of corporate data if they infiltrate BlackBerry devices connected to corporate assets.
As of February 2011 however, the ZeuS MitMo or Zbot Trojan currently targeting Symbian has also been compromising BlackBerrys. The crimeware injects a legitimately looking field into a web page and tricks users into giving out their mTANs (mobile transaction authentication numbers). This type of Trojan requires some social engineering on the part of the perpetrator. This combination of social and technical techniques shows that perpetrators are resourceful in side-stepping RIM’s strong authentication methods by ingeniously playing on user’s weaknesses, rather than on the device’s vulnerabilities.
More information can be found in the report “Mobile Device Security 2011-2016: Opportunities and Challenges” by Visiongain.
To order the report or ask for sample pages contact [email protected]
Contacts
MarketPublishers, Ltd.
Tanya Rezler
Tel: +44 208 144 6009
Fax: +44 207 900 3970
[email protected]
www.marketpublishers.com
Analytics & News
